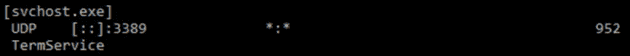One of the beauties of Qlik Sense Enterprise is that it can be installed on nearly any Windows machine, with very few pre-requisites.
One of the drawbacks is that you may then be tempted to load it onto a multi-purpose box, or at the very least, one with a number of core Windows roles installed (especially if you're just testing).
Uh oh, it's a 404
This post is going to offer some quick ways of resolving port clashes, and working out what's binding where without changing the core Qlik Sense Enterprise installation.
You may be able to solve this immediately by turning off a Windows role, or un-installing an application - some of the usual culprits include IIS, and the myriad of roles that rely on a core IIS install (including things like work folders and some remote connection roles).
Access all of the following through Start -> Command Prompt (CMD.EXE). An elevated prompt is recommended.
netsh
Netsh allows you to view or edit your network configuration, which in this case allows us to see bound ports and URLs.
netsh http show urlacl
The above command will list all "discretionary access control lists" for all reserved URLs, a single line of which is shown below.
Reserved URL: https://+:443/remoteDesktopGateway/
This tells us two things - both that something is bound to port 443 (default for HTTPS, which we need to connect to the QMC/hub/etc), and it gives us something to search for. A quick check for "remoteDesktopGateway" will show that this is a Windows role, which we can then either reconfigure or move to another server as needed.
netsh http show servicestate
This is similar to the above but states the registered URLs for that context, a single line of which is shown below.
Registered URLs: HTTP://LOCALHOST:9902/
It's worth bearing in mind that netsh does much more than the HTTP context shown here, giving access to most elements of Windows networking. For more information, have a look at the Microsoft Netsh overview.
netstat and tasklist
These two commands are useful for identifying offending processes, through identifying first the bound addresses, ports and process ID (PID), and second the source of that process.
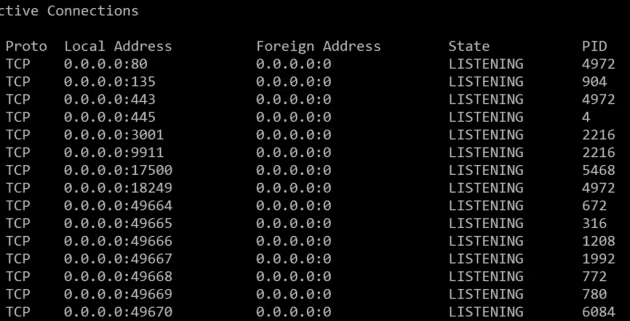
netstat -ano
Specifically, -a displays all active TCP connections and ports, -n displays active TCP connections, and -o displays associated PIDs.
The output of this command tells us the process ID - in the example below it shows port 80 and port 443 on PID 4972.
tasklist /svc
This command will provide you with a list of running processes and their associated PID (you can also get to this through the task manager). Looking up PID 4972 found above, the culprit in this case is Skype, which can be un-installed, or be reconfigured to avoid those ports. By using an elevated prompt, you can get the binary name of the executable as well, through calling netstat -ban.
In addition to the above, netstat can provide additional information through the use of further command line arguaments. Read more on this page about netstat (Windows XP+) at Microsoft.
There are a number of different ways to break this down further, which may be necessary if you've got multiple services running under a single PID (svchost, for example), which I'll cover in a later post. There are also additional tools on Windows Server like PowerShell, as well as non-microsoft Process Explorer apps that will let you delve deeper.
(note that this post was moved from the "dici" site and was originally published in April 2016)